A look at an evolving technology that has been changing how we communicate

It was February 2009. A 560 kg satellite named Iridium 33, whirling around the planet in the low earth orbit 789 km above the Taymyr Peninsula in Serbia, met a fatal end. It clashed with the defunct 900-kg Russian satellite, Kosmos 2251. This accident, the first of its kind, destroyed both the satellites and left behind thousands of fragments of debris, forming about 10 percent of all known space debris accumulated over the past 50-odd years. This is all the more poignant because it was an accident that could absolutely have been prevented.
Cryptography is the science of protecting sensitive data ̶ just like satellite locations, which can even be of national importance, especially if they have military applications. Rather than share such information directly with other countries, most countries share classified information about satellite locations with a trusted third party such as the US-based Analytical Graphics, which then advises satellite owners about possible collisions. But this approach may risk leaking of classified information. This is where cryptographers swoop into action. They build powerful tools to protect sensitive input data ̶ the satellite location, while still allowing two countries to collaborate ̶ calculating the likelihood of collisions, thus eliminating third parties from the equation. Perhaps if the makers of Iridium 33 and Kosmos 2251 had relied on cryptography, the landscape of outer space would look rather different today.
Cryptography enables secure communications because we live in the age of information and there is distrust in this world
Working on developing such cryptographic systems is Arpita Patra, Assistant Professor at the Department of Computer Science and Automation (CSA), IISc. According to her, cryptography enables secure communications because we live in the age of information and there is distrust in this world.
Her work, which enables distrusting parties to collaborate while still keeping their data private, is built on a sub-field of cryptography called Secure Multi-Party Computation (SMC). SMC’s foundations were laid in 1982 by a computer scientist, Andrew Yao (who later won a Turing Award), and finds applications beyond preventing satellite collisions. It could allow a startup to train its machine learning diagnostic app ̶ which requires feeding in tonnes of patient data ̶ while preventing the start-up from learning unique identifiers of the patient, including name, age or medical history. SMC could also set the stage for conducting fair e-elections or e-bidding: it lets people compute the number of votes or the highest bidding amount, without revealing names, votes or an individual’s bidding amount.

Cryptography wasn’t always this advanced. “Before the 1960-70s, cryptography was more an art than science,” explains Patra. But the basic idea behind safeguarding secret messages has been the same – a key – shielded by people who share a secret. Except that the key isn’t a physical construct but a mathematical one. The sender would lock or encrypt the message using the key, scrambling this message. Upon receiving this message, the receiver would use the same key to unlock or decrypt this message.
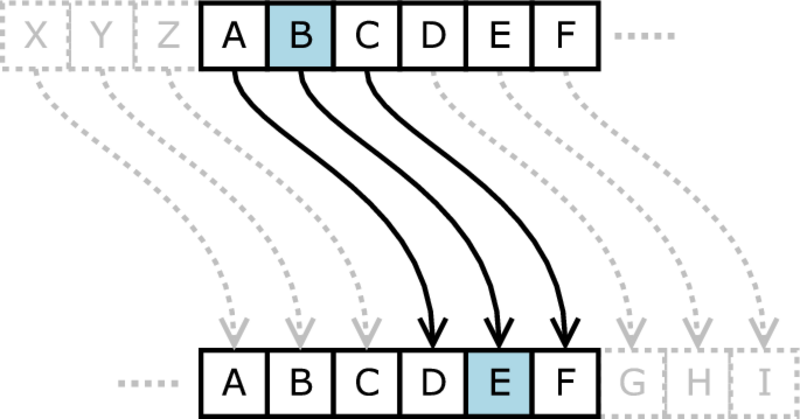
It is believed that Julius Caesar used a primitive form of cryptography, now called Caesar’s cipher, to communicate with his aides. To scramble or lock his secret message, Caesar substituted every letter with another letter by moving down the order of alphabets, by a set number. This number is the key. For example, if Caesar wanted to send ATTACK to his aid and if they had agreed upon a key ‘2’, the locked message would be CVVCEM. But this doesn’t mean an intruder couldn’t hazard a guess: it would take at most only 26 guesses to figure out the original message.
In the years that followed, cryptography began to evolve to cater to the needs of military organisations. Instead of using a single key to scramble the whole message, the new cryptographic algorithms or cryptosystems used different keys to scramble each letter in that message. If they wanted to send the same message ATTACK using a longer key 621098, then the locked message would be – GVUALS.
Such cryptographic systems, however, didn’t stand the test of time. Modern computers with high processing speed could easily break such systems. And in the 1990s the Internet began taking the world by storm and has since made some aspects of our lives effortless, from instant communication to online transactions. But the Internet’s Achilles’ heel is its open network, making private information – browsing history, bank account details, passwords, credit card information and the like – vulnerable to leaks and manipulation.
This created a need for stronger cryptosystems, which meant cryptographers had to come up with longer keys that would make modern computers stumble. Computers understand the binary language: they store and process data in binaries, only zeros and ones. So they built keys that were 256-bit long ̶ a bit is represented by a zero or a one. The breaking of 256-bit keys requires 2²⁵⁶ guesses at the most. It would take hundreds or even thousands of years for modern computers to crack this puzzle. But there’s a problem when the sender and the receiver use a single key for secure communication. They have to meet in private to agree upon a shared key, making it impractical. Or they have to use the Internet to share the key, increasing the risk of leaks.
So cryptographers tinkered with this concept and developed a more sophisticated cryptosystem that would rule out the need to share keys. That would pave the way for online transactions and set a platform for e-commerce companies to flourish. This new system, called Public Key Cryptography (PKC), would soon become ubiquitous in the lives of common people. It would find takers from private organisations, hospitals, and banks, to WhatsApp.
The feature that sets PKC apart is that instead of using one key, PKC employs one set of keys: public and private. The public key which is used to lock a secret is known to everyone, while the private key is used to unlock a secret. Talking about WhatsApp’s end-to-end encryption, Sanjit Chatterjee, Associate Professor at CSA, explains, “You will have a public key, so to say, known to everybody. There will be some kind of mapping based on your mobile phone number which will give you some identity, then there will be a public key, which will be useful to lock messages that you can send out. The corresponding message that you receive can only be unlocked by you because your private key is only known to you.”
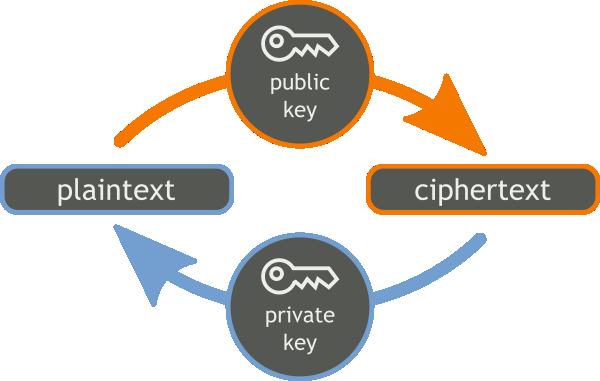
Another widely used application of PKC is to ensure secure browsing on websites such as those of banks or e-commerce companies. The public key functions as a website’s identity card, which is verified by a certifying authority. This appears in the form of a lock on the address bar of your browser. The lock and the certificate assure users that they are on an authentic website and any information exchanged, including passwords, will remain private, adds Chatterjee.
Explaining how keys achieve this, he says that the public and private keys have a mathematical relationship. This relationship is centered on the difficulty in certain mathematical problems such as finding prime factors of large numbers. Prime factors of 10, for example, are 2 and 5. This is easy to figure out for a number this small, but as the number gets larger, finding the right factors presents a formidable challenge, even for a modern computer. The American company that commercialised this system, RSA Security LLC, launched the RSA Factoring Challenge in 1991. And people haven’t been successful in factoring the larger numbers. The challenge is closed now, but it does show that some of the cryptosystems that we have today are close to inviolable.
Can a system remain secure even when an intruder or adversary uses brute force to try to break it? This is something Bhavana Kanukurthi, Assistant Professor at CSA, is focusing on. This domain of study is called Information-Theoretic Cryptography. The goal of this field is to ensure that even with computers with unlimited computing power, the adversary will not be able to break into the system.
Another feature of Information-Theoretic Cryptography is developing systems that can withstand quantum computers – computers with the ability to topple current cryptosystems. Modern computers have limited computing powers because they can either run a zero or one at a time. On the other hand, quantum computers which run on qubits, can be in a combination of zero and one simultaneously, making them faster and powerful.
“The cryptosystems that we develop should be able to fight an adversary with access to a quantum computer”
While researchers predict that it could take more than 15 years for quantum computers to become widely practical, Chatterjee thinks it is important to be cautious. “After 15 years, if somebody develops a quantum computer and if we don’t have a cryptosystem that is resistant to these computers, then all our data will leak. You cannot switch over to a new system overnight.” His research focuses on developing a quantum-safe cryptosystem that can run on modern computers. “The cryptosystems that we develop should be able to fight an adversary with access to a quantum computer.”
To make quantum-safe cryptosystems a reality, cryptographers and cryptoanalysts have to work together. “We [the cryptographic community] have some candidates. The cryptographer will build the cryptosystem while the analysts will try to break it. We are discussing, debating and writing papers. And slowly some consensus will emerge. There will be a certain system which people will accept, which can be used. People will still improve upon it and make replacements. So this game continues,” he says.
Just like Chatterjee, Patra and her team are trying to build efficient cryptosystems. In her case, she aims to make SMC usable in a practical context. Denmark was the first country to use SMC, to help with their sugar beet auctioning. While some countries have already started embracing SMC, India hasn’t yet.
From her collaborator at UC Berkeley, Patra learned that banks and hospitals in the US have technical teams that are constantly on a look out for the latest developments in cryptography. These teams stay in touch with cryptographers in universities, and once they are convinced of the capabilities of SMC, they take it up with their institutions. Patra suggests that India does the same. “A lot of talking has to happen, we need to understand their [banks’ or hospitals’ or government organisations’] problems and tell them how our technology will fit in. But the reach has not yet happened.”
While the goal of SMC is to eliminate the need for a third party, it also becomes important to ensure consensus among the collaborators. Called distributed consensus systems, it also finds its use in the world of digital currency or cryptocurrency: users don’t pay a fee every time they transact with each other, they can make global transactions in shorter periods, and the technology is bolstered by cryptography. When people use cryptocurrency, they perform transactions by doing away with third parties such as banks. Blockchains replace banks – they serve as online diaries holding records of transactions made by people – and are accessible to all their users.
“Everyone is part of the same network and all of them can maintain the data, making it democratic in nature,” says Patra. But one of the major issues with blockchain that researchers, including Patra, are grappling with is consensus, which is to get the records of all the participants or collaborators in sync with each other every time someone makes a transaction. Sometimes, the records don’t get updated, due to some error. In such cases, there are chances that a participant can cheat by spending a given set of coins twice. So Patra and her team are aiming to build a technology that guarantees that all the participants will reach a consensus over a transaction.
Most of what cryptographers at research Institutes come up with are proof of concepts. Bringing them into practice demands more expertise, which falls outside their domain. Elaborating further, Patra says, “ A lot of people, including security experts, computer security experts and software security experts have to come together to make cryptosystems really secure”.